

| Vulnerabilities | Checklists | 800-53/800-53A | Product Dictionary | Impact Metrics | Data Feeds | Statistics |
| Home | SCAP | SCAP Validated Tools | SCAP Events | About | Contact | Vendor Comments |


|
||||||||||||||
|
NVD contains:
| 55069 | CVE Vulnerabilities |
| 202 | Checklists |
| 231 | US-CERT Alerts |
| 2690 | US-CERT Vuln Notes |
| 8140 | OVAL Queries |
Last updated: 02/13/13
CVE Publication rate:
17 vulnerabilities / dayNVD provides five mailing lists to the public. For information and subscription instructions please visit NVD Mailing Lists
NVD is a product of the NIST Computer Security Division and is sponsored by the Department of Homeland Security’s National Cyber Security Division. It supports the U.S. government multi-agency (OSD, DHS, NSA, DISA, and NIST) Information Security Automation Program. It is the U.S. government content repository for the Security Content Automation Protocol (SCAP).
The Common Weakness Enumeration Specification (CWE) provides a common language of
discourse for discussing, finding and dealing with the causes of software security
vulnerabilities as they are found in code, design, or system architecture. Each individual
CWE represents a single vulnerability type. CWE is currently maintained by the
MITRE
Corporation with support from the National Cyber Security Division (DHS).
A detailed CWE list is currently available at the
MITRE website; this list provides a detailed definition for each individual CWE.
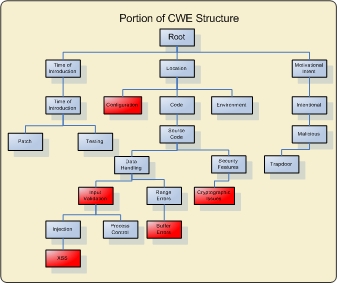
All individual CWEs are held within a hierarchical structure that allows for multiple levels of abstraction. CWEs located at higher levels of the structure (i.e. Configuration) provide a broad overview of a vulnerability type and can have many children CWEs associated with them. CWEs at deeper levels in the structure (i.e. Cross Site Scripting) provide a finer granularity and usually have fewer or no children CWEs. The image to the right represents a portion of the overall CWE structure, the red boxes represent the CWEs being used by NVD. (click to enlarge). NVD integrates CWE into the scoring of CVE vulnerabilities by providing a cross section of the overall CWE structure. NVD analysts score CVEs using CWEs from different levels of the hierarchical structure. This cross section of CWEs allows analysts to score CVEs at both a fine and coarse granularity, which is necessary due to the varying levels of specificity possessed by different CVEs. The cross section of CWEs used by NVD is listed below; each CWE listed links to a detailed description hosted by MITRE. For a better understanding of how the standards link together please visit: MITRE - Making Security Measurable CWE is not currently part of the Security Content Automation Protocol (SCAP). NVD is using CWE as a classification mechanism that differentiates CVEs by the type of vulnerability they represent. |
| Name | CWE-ID | Description |
|---|---|---|
| Authentication Issues | CWE-287 | Failure to properly authenticate users. |
| Credentials Management | CWE-255 | Failure to properly create, store, transmit, or protect passwords and other credentials. |
| Permissions, Privileges, and Access Control | CWE-264 | Failure to enforce permissions or other access restrictions for resources, or a privilege management problem. |
| Buffer Errors | CWE-119 | Buffer overflows and other buffer boundary errors in which a program attempts to put more data in a buffer than the buffer can hold, or when a program attempts to put data in a memory area outside of the boundaries of the buffer. |
| Cross-Site Request Forgery (CSRF) | CWE-352 | Failure to verify that the sender of a web request actually intended to do so. CSRF attacks can be launched by sending a formatted request to a victim, then tricking the victim into loading the request (often automatically), which makes it appear that the request came from the victim. CSRF is often associated with XSS, but it is a distinct issue. |
| Cross-Site Scripting (XSS) | CWE-79 | Failure of a site to validate, filter, or encode user input before returning it to another user’s web client. |
| Cryptographic Issues | CWE-310 | An insecure algorithm or the inappropriate use of one; an incorrect implementation of an algorithm that reduces security; the lack of encryption (plaintext); also, weak key or certificate management, key disclosure, random number generator problems. |
| Path Traversal | CWE-22 | When user-supplied input can contain “..” or similar characters that are passed through to file access APIs, causing access to files outside of an intended subdirectory. |
| Code Injection | CWE-94 | Causing a system to read an attacker-controlled file and execute arbitrary code within that file. Includes PHP remote file inclusion, uploading of files with executable extensions, insertion of code into executable files, and others. |
| Format String Vulnerability | CWE-134 | The use of attacker-controlled input as the format string parameter in certain functions. |
| Configuration | CWE-16 | A general configuration problem that is not associated with passwords or permissions. |
| Information Leak / Disclosure | CWE-200 | Exposure of system information, sensitive or private information, fingerprinting, etc. |
| Input Validation | CWE-20 | Failure to ensure that input contains well-formed, valid data that conforms to the application’s specifications. Note: this overlaps other categories like XSS, Numeric Errors, and SQL Injection. |
| Numeric Errors | CWE-189 | Integer overflow, signedness, truncation, underflow, and other errors that can occur when handling numbers. |
| OS Command Injections | CWE-78 | Allowing user-controlled input to be injected into command lines that are created to invoke other programs, using system() or similar functions. |
| Race Conditions | CWE-362 | The state of a resource can change between the time the resource is checked to when it is accessed. |
| Resource Management Errors | CWE-399 | The software allows attackers to consume excess resources, such as memory exhaustion from memory leaks, CPU consumption from infinite loops, disk space consumption, etc. |
| SQL Injection | CWE-89 | When user input can be embedded into SQL statements without proper filtering or quoting, leading to modification of query logic or execution of SQL commands. |
| Link Following | CWE-59 | Failure to protect against the use of symbolic or hard links that can point to files that are not intended to be accessed by the application. |
| Other | No Mapping | NVD is only using a subset of CWE for mapping instead of the entire CWE, and the weakness type is not covered by that subset. |
| Not in CWE | No Mapping | The weakness type is not covered in the version of CWE that was used for mapping. |
| Insufficient Information | No Mapping | There is insufficient information about the issue to classify it; details are unkown or unspecified. |
| Design Error | No Mapping | A vulnerability is characterized as a “Design error” if there exists no errors in the implementation or configuration of a system, but the initial design causes a vulnerability to exist. |