The Federal Identity, Credential and Access Management Subcommittee Announces the ICAM Information Sharing Day and Vendor Expo
On November 27th, the Identity, Credential, and Access Management Subcommittee (ICAMSC) will hold the ICAM Information Sharing Day and Vendor Expo. The focus of this ICAM Information Day and Vendor Expo will be the use of PIV credentials in systems such as Physical Access Control Systems (PACS), Logical Access Control Systems (LACS), mobile devices and cloud services. The participating vendors will demonstrate their latest information assurance and security products and services related to the use of the PIV.
LOGISTICS/VENUE INFORMATION
The ICAM Information Day and Vendor Expo will be held on November 27, 2012 in coordination with the Smart Cards in Government Conference which will be held November 28th – 30th at the following location:
Washington Convention Center
801 Mount Vernon Place Northwest, Washington, DC 20001
There will be no fee for federal employees and contractors with PIV attending the ICAM Information Day event.
REGISTRATION INFORMATION
Those attending ICAM Information Day and Vendor Expo should register at the following site: www.GovSmartID.com
AGENDA
Please note that the agenda is subject to change.
|
Timeframe |
Description |
Speaker |
|
9:00 – 9:15 |
Welcome and Opening Remarks |
Deb Gallagher (GSA) and/or Paul Grant (DoD) |
|
9:15 – 10:00 |
Keynote Address: Enabling CAC/PIV in a Mobile Government Workforce |
Rob Carey (DoD) |
|
10:00 – 12:00 |
Opening of the Vendor Exhibits |
|
|
12:00 – 12:30 |
Lunch break (lunch not provided) |
|
|
12:30 – 1:00 |
Security Policy and Standards for Use of Mobile Devices on Federal Networks |
Carol Bales (OMB)/ Donna Dodson (NIST) |
|
1:00 – 1:30 |
Expectation of PIV use with Logical Access Systems |
Bill Erwin (DoD) |
|
1:30 – 2:00 |
Expectation of PIV use with Mobile Devices |
Deb Gallagher (GSA) |
|
2:00 – 2:30 |
Expectation of PIV use with Physical Access Systems |
Will Morrison (FAA) |
|
2:30 – 3:00 |
Afternoon Break (vendor exhibits will remain open) |
|
|
3:00 – 3:15 |
FIPS 201-2 Status |
Hilde Ferraiolo (NIST) |
|
3:15 – 3:30 |
Update on FY FISMA Metrics for PIV Use |
Glen Lee (DOE)/ Rajeev Pillai ( GSA) |
|
3:30 – 3:45 |
Trust Framework Update |
Anil John (GSA) |
|
3:45 – 4:15 |
Open Discussion |
Deb Gallagher (GSA) and/or Paul Grant (DoD) |
|
4:15 – 4:30 |
Closing Remarks |
Deb Gallagher (GSA) and/or Paul Grant (DoD) |
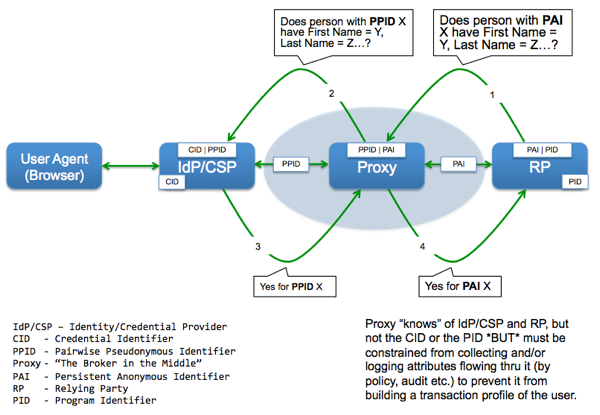
 For the federal government to utilize industry standards, they need to be widely deployed by multiple vendors, interoperable, and meet the security and privacy policy requirements articulated by authoritative federal government bodies such as OMB, NIST, CIO Council etc.
For the federal government to utilize industry standards, they need to be widely deployed by multiple vendors, interoperable, and meet the security and privacy policy requirements articulated by authoritative federal government bodies such as OMB, NIST, CIO Council etc.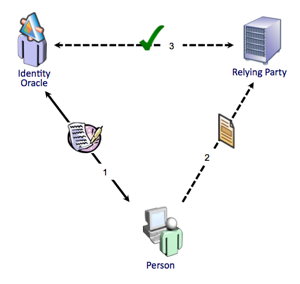
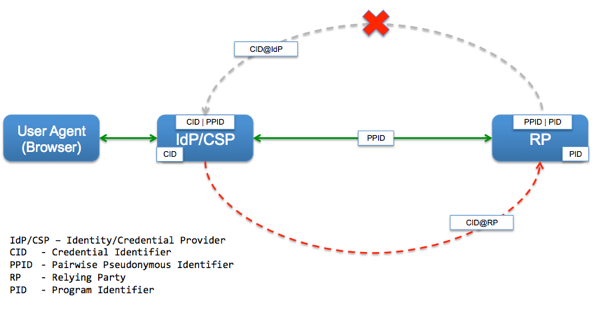
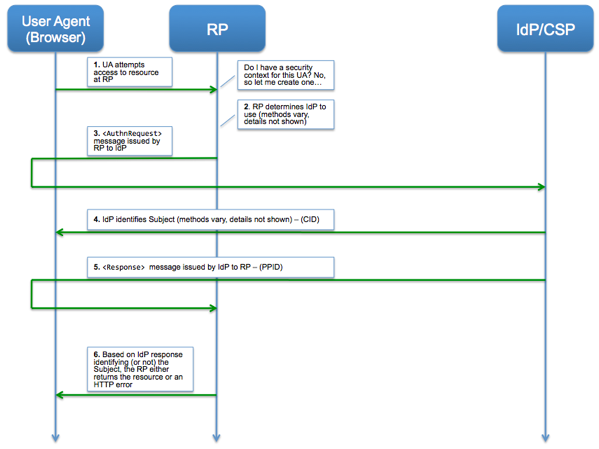
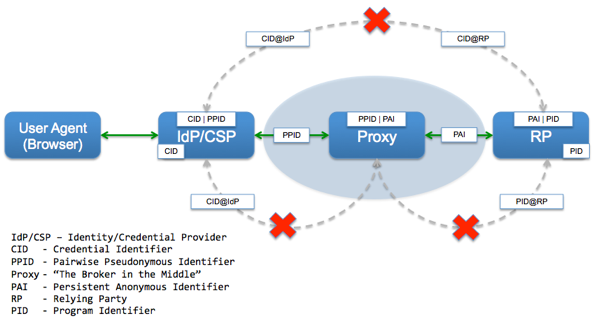
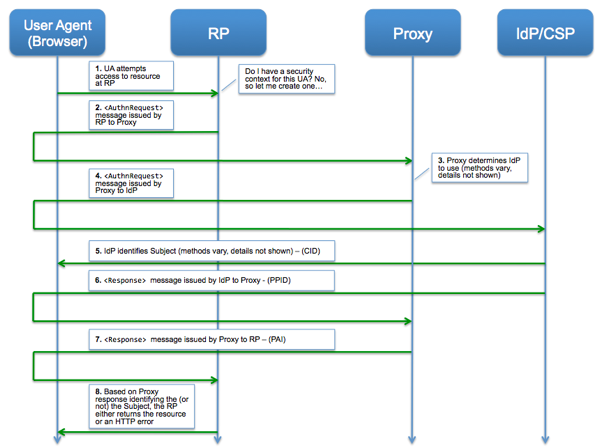
 NIST, in its
NIST, in its  What is the minimum set of attributes needed to uniquely identify a person within a system?
What is the minimum set of attributes needed to uniquely identify a person within a system? How will you move the verified attributes from an IdP/CSP/AP to the RP?
How will you move the verified attributes from an IdP/CSP/AP to the RP?