Overview of Cyber Vulnerabilities
Control systems are vulnerable to cyber attack from inside and outside the control system network. To understand the vulnerabilities associated with control systems you must know the types of communications and operations associated with the control system as well as have an understanding of the how attackers are using the system vulnerabilities to their advantage. This discussion provides a high level overview of these topics but does not discuss detailed exploits used by attackers to accomplish intrusion.
- Understanding Control System Cyber Vulnerabilities
- Access to the Control System LAN
- Discovery of the Process
- Control of the Process
Understanding Control System Cyber Vulnerabilities
To understand the vulnerabilities associated with control systems (CS), you must first know all of the possible communications paths into and out of the CS. Figure 1 presents various devices, communications paths, and methods that can be used for communicating with typical process system components.

large version
Figure 1: Communications access to control systems
As illustrated in Figure 1, there are many ways to communicate with a CS network and components using a variety of computing and communications equipment. A person who is knowledgeable in process equipment, networks, operating systems and software applications can use these and other electronic means to gain access to the CS. Wireless access points that allow unauthorized connection to system components and networks present vulnerabilities.
In a typical large-scale production system utilizing SCADA or Distributed Control System (DCS) configuration there are many computer, controller and network communications components integrated to provide the operational needs of the system. A typical network architecture is shown in Figure 2.
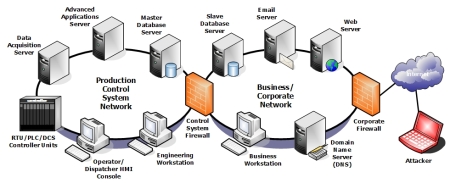
large version
Figure 2: Typical two-firewall network architecture
Controller units connect to the process devices and sensors to gather status data and provide operational control of the devices. The controller unit communicates to a CS data acquisition server using various communications protocols (structured formats for data packaging for transmission). Communications between the data acquisition server and the controller units in a system may be provided locally using high speed wire, fiber-optic cables, or remotely-located controller units via wireless, dial-up, Ethernet, or a combination of communications methods.
The operator or dispatcher monitors and controls the system through the Human-Machine Interface (HMI) subsystem. The HMI provides graphical displays for presentation of status of devices, alarms and events, system health, and other information relevant to the system. The operator can interact with the system through the HMI displays to remotely operate system equipment, troubleshoot problems, develop and initiate reports, and perform other operations.
System data is collected, processed and stored in a master database server. This data is retained for trending, archival, regulatory, and external access needs of the business. The types of data include data from the following sources: the data acquisition server, operator control interactions, alarms and events, and calculated and generated from other sources.
Most control systems utilize specialized applications for performing operational and business related data processing. These tasks are typically performed on advanced applications servers pulling data from various sources on the control system network. These applications can result in real-time operational control adjustments, reports, alarms and events, calculated data source for the master database server archival, or support of real-time analysis work being performed from the engineering workstation or other interface computers.
An engineering workstation provides a means to monitor and troubleshoot various aspects of the system operation, install and update program elements, recover from failures, and miscellaneous tasks associated with system administration.
A mission-critical control system is typically configured in a fully-redundant architecture allowing quick recovery from loss of various components in the system. A backup control center is used in more critical applications to provide a secondary control system if there is a catastrophic loss of the main system.
The control system network is often connected to the business office network to provide real-time transfer of data from the control network to various elements of the corporate office. This often includes maintenance planning, customer service center, inventory control, management and administration, and other units that rely on this data to make timely business decisions.
An attacker who wishes to assume control of a control system is faced with three challenges:
- Gain access to the control system LAN
- Through discovery, gain understanding of the process
- Gain control of the process.
Access to the Control System LAN
The first thing an attacker needs to accomplish is to bypass the perimeter defenses and gain access to the control system LAN. Most control system networks are no longer directly accessible remotely from the Internet. Common practice in most industries has a firewall separating the business LAN from the control system LAN. This not only helps keep hackers out, it isolates the control system network from outages, worms, and other afflictions that occur on the business LAN. Most of the attacker's off-the-shelf hacking tools can be directly applied to the problem. There are a number of common ways an attacker can gain access, but the miscellaneous pathways outnumber the common pathways.
Common Network Architectures

large
version
Figure 3: Two firewalls
There are three common architectures found in most control systems. Every business has its own minor variations dictated by their environment. All three are securable if the proper firewalls, intrusion detection systems, and application level privileges are in place. By far the most common architecture is the two-firewall architecture (see Figure 3). The business LAN is protected from the Internet by a firewall and the control system LAN is protected from the business LAN by a separate firewall. The business firewall is administered by the corporate IT staff and the control system firewall is administered by the control system staff.

large version
Figure 4: Control System as DMZ
The second most common architecture is the control system network as a Demilitarized Zone (DMZ) off the business LAN (see Figure 4). A single firewall is administered by the corporate IT staff that protects the control system LAN from both the corporate LAN and the Internet.
Large DCS often need to use portions of the business network as a route between multiple control system LANs (see Figure 5). Each control system LAN typically has its own firewall protecting it from the business network and encryption protects the process communication as it travels across the business LAN. Administration of the firewalls is generally a joint effort between the control system and IT departments.

large version
Figure 5: Business LAN as backbone

large version
Figure 6: Data DMZ
A new trend is to install a data DMZ between the corporate LAN and the control system LAN (see Figure 6). This provides an added layer of protection because no communications take place directly from the control system LAN to the business LAN. The added strength of a data DMZ is dependent on the specifics of how it is implemented.
Dial-up Access to the RTUs

large version
Figure 7: Dial-up access to the RTUs
One of the most common routes of entry is directly dialing modems attached to the field equipment (see Figure 7). Modems are used as backup communications pathways if the primary high-speed lines fail. The attacker dials every phone number in a city looking for modems. Additionally, an attacker will dial every extension in the company looking for modems hung off the corporate phone system. Most Remote Terminal Units (RTUs) identify themselves and the vendor who made them. Most RTUs require no authentication or a password for authentication. It is common to find RTUs with the default passwords still enabled in the field.
The attacker must know how to speak the RTU protocol to control the RTU. Control is generally, but not always, limited to a single substation.
Vendor Support
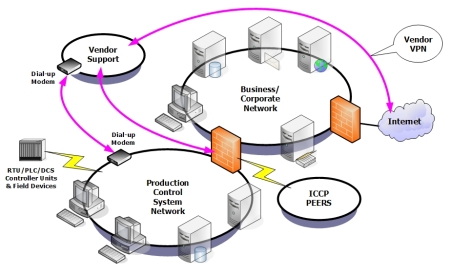
large version
Figure 8: Vendor support
Most control systems come with a vendor support agreement. There is a need for support during upgrades or when a system is malfunctioning. The most common means of vendor support used to be through a dial-up modem and PCAnywhere (see Figure 8). In recent years, that has transitioned to VPN access to the control system LAN. An attacker will attempt to gain access to internal vendor resources or field laptops and piggyback on the connection into the control system LAN.
IT Controlled Communication Gear

large version
Figure 9: IT Controlled Communication Gear
Often it is the responsibility of the corporate IT department to negotiate and maintain long-distance communication lines. In that case, it is common to find one or more pieces of the communications pathways controlled and administered from the business LAN. Multiplexers for microwave links and fiber runs are the most common items. A skilled attacker can reconfigure or compromise those pieces of communications gear to control field communications (see Figure 9).
Corporate VPNs

large version
Figure 10: Corporate VPNs
Most control systems have some mechanism for engineers on the business LAN to access the control system LAN. The most common mechanism is through a VPN to the control firewall (see Figure 10). An attacker will attempt to take over a machine and wait for the legitimate user to VPN into the control system LAN and piggyback on the connection.
Database Links

large version
Figure 11: Database links
Nearly every production control system logs to a database on the control system LAN that is then mirrored into the business LAN. Often administrators go to great lengths to configure firewall rules, but spend no time securing the database environment. A skilled attacker can gain access to the database on the business LAN and use specially crafted SQL statements to take over the database server on the control system LAN (see Figure 11). Nearly all modern databases allow this type of attack if not configured properly to block it.
Poorly Configured Firewalls
Often firewalls are poorly configured due to historical or political reasons. Common firewall flaws include passing Microsoft Windows networking packets, passing rservices, and having trusted hosts on the business LAN. The most common configuration problem is not providing outbound data rules. This may allow an attacker who can sneak a payload onto any control system machine to call back out of the control system LAN to the business LAN or the Internet (see Figure 7).
Peer Utility Links

large version
Figure 12: Peer utility links
Often the easiest way onto a control system LAN is to take over neighboring utilities or manufacturing partners. Historically, links from partners or peers have been trusted. In that case, the security of the system is the security of the weakest member (see Figure 12). Recently, peer links have been restricted behind firewalls to specific hosts and ports.
Discovery of the Process
An attacker that gains a foothold on the control system LAN must discover the details of how the process is implemented to surgically attack it. If a dozen chemical engineers were tasked with creating a talcum powder plant, each of them would use different equipment and configure the equipment in a unique way. An attacker that wants to be surgical needs the specifics in order to be effective. An attacker that just wants to shut down a process needs very little discovery.
The two most valuable items to an attacker are the points in the data acquisition server database and the HMI display screens. Each control system vendor calls the database something different, but nearly every control system assigns each sensor, pump, breaker, etc., a unique number. On the communications protocol level, the devices are simply referred to by number. A surgical attacker needs a list of the point reference numbers in use and the information required to assign meaning to each of those numbers.
The operator HMI screens generally provide the easiest method for understanding the process and assignment of meaning to each of the point reference numbers. Each control system vendor is unique in where it stores the operator HMI screens and the points database. Rules added to the Intrusion Detection System (IDS) looking for those files are effective in spotting attackers.
Control of the Process
Sending Commands Directly to the Data Acquisition Equipment
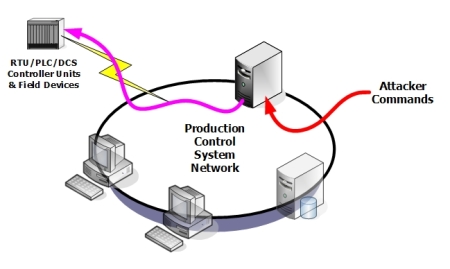
large version
Figure 13: Sending commands directly to the data acquisition equipment
The easiest way to control the process is to send commands directly to the data acquisition equipment (see Figure 13). Most PLCs, protocol converters, or data acquisition servers lack even basic authentication. They generally accept any properly formatted command. An attacker wishing control simply establishes a connection with the data acquisition equipment and issues the appropriate commands.
Exporting the HMI Screen

large version
Figure 14: Exporting the HMI screen
An effective attack is to export the screen of the operator's HMI console back to the attacker (see Figure 14). Off-the-shelf tools can perform this function in both Microsoft Windows and Unix environments. The operator will see a "voodoo mouse" clicking around on the screen unless the attacker blanks the screen. The attacker is also limited to the commands allowed for the currently logged-in operator. For instance, he probably could not change the phase tap on a transformer.
Changing the Database

large version
Figure 15: Changing the database
In some, but not all, vendor's control systems, manipulating the data in the database can perform arbitrary actions on the control system (see Figure 15).
Man-in-the-Middle Attacks
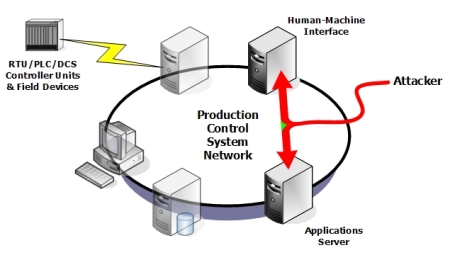
large version
Figure 16: Man-in-the-middle attacks
Man-in-the-middle attacks can be performed on control system protocols if the attacker knows the protocol he is manipulating. An attacker can modify packets in transit, providing both a full spoof of the operator HMI displays and full control of the control system (see Figure 16). By inserting commands into the command stream the attacker can issue arbitrary or targeted commands. By modifying replies, the operator can be presented with a modified picture of the process.