| * |
|
Seamless and Secure Mobility
Summary:The problem we are facing is how to interconnect a wide variety of heterogeneous and un-interoperable networks including wired and wireless networks in order to provide users with ubiquitous connectivity and the ability to roam seamlessly and securely across networks of different types. Our long-term goals are to bridge the technological and measurement gaps between stovepipe and heterogeneous network technologies in order to allow for better interconnectivity, seamless interoperability, and better support for network connectivity and mobility services. Description:There is a wide variety of disjoint network types for example, Wi-Fi, WiMAX, Bluetooth, ZigBee and cellular networks (2.5G, 3G, 4G). However, most implementations are developed for single vendor platforms and do not allow for equipment interoperability. Key obstacles to seamless mobility include:
Technical ApproachOur technical approach consists of considering complex protocol interactions and cross-layer techniques and the use of advanced measurement in order to accurately assess and manage the performance and security characteristics of mobility protocols.
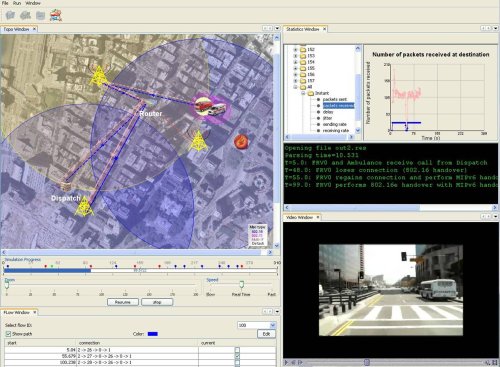
Cross-layer protocol interactionsThis work supports the IEEE 802.21 working group on Media Independent Handovers (MIH). After participating in the group's activities for over two years, we completed edits to the IEEE 802.21 draft specification as part of final sponsor letter balloting. The draft was published as a standard in January, 2009. IP mobility supportIn this effort we are developing analytical and simulation tools and models in order to evaluate the performance of different IP mobility protocols and some of their extensions currently being considered at the IETF. Since cross-layer protocol interactions are key to achieving seamless and secure mobility, much attention is devoted to developing effective measurement techniques for capturing and characterizing these interactions. Similarly, abstraction models for the radio propagation, PHY, MAC, IP, and TCP layers are designed in order to accelerate the development and evaluation of mobility protocols. These models are validated against laboratory experimentation and prototype implementations. Secure mobilityThere are several factors that affect the implementation of security mechanisms and how they are characterized and measured in different types of networks. Our efforts in this area are aimed at:
Mobility information servicesInformation services are key to achieving timely handovers and seamless mobility. We are investigating potential information service architectures and methods for accessing and distributing secure mobility information. We are developing measurement techniques and models for characterizing performance trade-offs. Major Accomplishments:Contributions to Standards Developing Organizations
Technical DevelopmentsANTD assists in the completion of the IEEE 802.21 Media Independent Handovers (MIH) draft
|
End Date:ongoingLead Organizational Unit:itlCustomers/Contributors/Collaborators:Associated Products:Contact
Advanced Network Technologies Division 100 Bureau Drive, M/S 8920 301-975-4190 Telephone |
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||